- (a)
- Give the best upper bound you can (using big Oh notation) on the amount of money we will need to initially invest in the tree T in order to make sure the Money Invariant holds. (The Money Invariant says that each node has a number of dollars equal to its rank).
- (b)
- Use your answer to part (a) to give the best bound you can (using Big Oh notation) on the total cost of performing m Lookup operations using the Splay tree algorithm, starting with the tree T (as opposed to starting with an empty tree).
- (a)
- What is the primary advantage of public-key cryptography over symmetric
cryptography?
- (b)
- Consider a message M encrypted using the RSA public-key cryptosystem. Let
E(M) be the ciphertext produced.
Give an algorithm for determining M. What is the running time of your
algorithm as a function of the number of bits in n (the modulus =pq)?
- (c)
- To encrypt a plaintext M using the RSA public-key cryptosystem, the message is first broken up into chunks of at most k bits, where k is the number of bits in the modulus n. Why can't we just encrypt the entire message in one fell swoop?
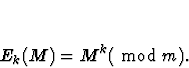
Let s be the mod
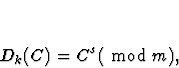
where C= Ek(M).
- (a)
- Prove that the cryptosystem works, i.e., that Dk(C) = M.
- (b)
- Characterize the set of keys k <m for which this system works.
- (c)
- Give an argument for why this cryptosystem is probably not vulnerable to
known plaintext attack (i.e., recovering the key, given a message and
its encryption).