|

CSE 461: Introduction to Computer Communication Networks, Spring 2013 |
|
|
|
|
|
|
Homework 3 – TCP ObjectiveTo see the details of TCP (Transmission Control Protocol). TCP is the main transport layer protocol used in the Internet. It is covered in §6.5 of your text. You might want to review that section before doing this lab. RequirementsWireshark: This lab uses Wireshark to capture or examine a packet trace. A packet trace is a record of traffic at some location on the network, as if a snapshot was taken of all the bits that passed across a particular wire. The packet trace records a timestamp for each packet, along with the bits that make up the packet, from the low-layer headers to the higher-layer contents. Wireshark runs on most operating systems, including Windows, Mac and Linux. It provides a graphical UI that shows the sequence of packets and the meaning of the bits when interpreted as protocol headers and data. The packets are color-coded to convey their meaning, and Wireshark includes various ways to filter and analyze them to let you investigate different aspects of behavior. It is widely used to troubleshoot networks. You can download Wireshark from www.wireshark.org if it is not already installed on your computer. We highly recommend that you watch the short, 5 minute video “Introduction to Wireshark” that is on the site. wget / curl:
This lab
uses wget (Linux and Windows) and curl (Mac) to fetch web resources. wget and curl are command-line programs that let you fetch a URL.
Unlike a web browser, which fetches and executes entire pages, wget and curl give you control over exactly which
URLs you fetch and when you fetch them.
Under Linux, wget can be installed via your package manager. Under
Windows, wget is available as a binary; look for download
information on http://www.gnu.org/software/wget/. Under Mac, curl comes installed with the OS. Both have
many options (try “wget --help” or “curl --help” to see) but a URL can be fetched simply with “wget URL” or “curl URL ”. Browser: This lab uses a
web browser to find or fetch pages as a workload. Any web browser will do. Trace File: To answer the
questions, use the provided trace file. It can be found here.
Step 1: Capture a Trace [optional]Proceed as follows to capture a trace of a single TCP connection that sends a moderate amount of data; alternatively, you may use a supplied trace. Many applications use TCP as a transport, including web browsers. So we will simply perform a web download to exercise a TCP connection. However, note that TCP is able to transfer data in both directions at the same time, but with a download content is only sent from the remote server the local computer (after the initial request). 1. Find a URL of a single moderately-sized resource, and that you can download using HTTP (rather than HTTPS). You may use your browser to search, perhaps looking for a picture (.jpg) or PDF document (.pdf). You want to ensure that it is a single resource and not a web page (e.g., a .html) with many inlined resources. As a suggestion, the SIGCOMM conference makes its technical papers available as PDF files. Find the URL of an interesting networking paper! 2. Fetch the URL with wget or curl to check that you are able to retrieve at least 500 KB of content over at least several of network time seconds. For example, use the command “wget http://sigcomm.org/paper.pdf” or “curl http://sigcomm.org/paper.pdf > file”. If the fetch does not work then try a different URL; keep in mind that you may be referring to a URL by a shortcut for which browsers must do work to find the intended content, e.g., http://mit.edu/image.jpg may really be http://web.mit.edu/image.jpg. Successful examples of fetching are shown in the figures below.
Figure 1: A successful fetch of a web resource with wget (Windows)
Figure 2: A successful fetch of a web resource with curl (Mac) 3. Launch Wireshark and start a capture with a
filter of “tcp and host xx.xx.xx”, where xx.xx.xx is the name of the remote server from which
you will fetch content, e.g., “conferences.sigcomm.org” in the figure showing our example below.
The idea of the filter is to only capture TCP traffic between your computer and
the server. Your
capture window should be similar to the one pictured below, other than our
highlighting. Select the interface from which to capture as the main wired or
wireless interface used by your computer to connect to the Internet. If unsure,
guess and revisit this step later if your capture is not successful. Uncheck
“capture packets in promiscuous mode”. This mode is useful to overhear packets
sent to/from other computers on broadcast networks. We only want to record
packets sent to/from your computer. Leave other options at their default
values. The capture filter, if
present, is used to prevent the capture of other traffic your computer may send
or receive. On Wireshark 1.8, the capture filter box is present directly on the
options screen, but on Wireshark 1.9, you set a capture filter by
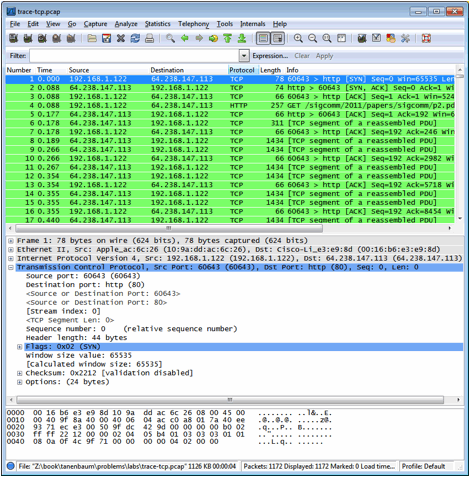
double-clicking on the interface. Figure 3: Setting up the capture options 4. After the capture is started, repeat the wget/curl command above. This time, the packets will also be recorded by Wireshark. 5. When the command is complete, return to Wireshark and use the menus or buttons to stop the trace. You should now have a trace similar to that shown in the figure below. We have expanded the detail of the TCP header in our view, since it is our focus for this lab.
Figure 4: Trace of TCP traffic showing the details of the TCP header Step 2: Inspect the TraceSelect a long packet anywhere in the middle of your trace whose protocol is listed as TCP. Expand the TCP protocol section in the middle panel (by using the “+” expander or icon). All packets except the initial HTTP GET and last packet of the HTTP response should be listed as TCP. Picking a long packet ensures that we are looking at a download packet from the server to your computer. Looking at the protocol layers, you should see an IP block before the TCP block. This is because the TCP segment is carried in an IP. We have shown the TCP block expanded in our figure. You will see roughly the following fields: Š First comes the source port, then the destination port. This is the addressing that TCP adds beyond the IP address. The source port is likely to be 80 since the packet was sent by a web server and the standard web server port is 80. Š Then there is the sequence number field. It gives the position in the bytestream of the first payload byte. Š Next is the acknowledgement field. It tells the last received position in the reverse byte stream. Š The header length giving the length of the TCP header. Š The flags field has multiple flag bits to indicate the type of TCP segment. You can expand it and look at the possible flags. Š Next is a checksum, to detect transmission errors. Š There may be an Options field with various options. You can expand this field and explore if you would like, but we will look at the options in more detail later. Š Finally, there may be a TCP payload, carrying the bytes that are being transported. As well as the above fields, there may be other informational lines that Wireshark provides to help you interpret the packet. We have covered only the fields that are carried across the network. Step 3: TCP Segment StructureTo show your understanding of TCP, sketch a figure of the TCP segment you studied. It should show the position and size in bytes of the TCP header fields you can observe using Wireshark, as well as the TCP payload. Do not break down the Flags field, or any Options field, and if you find that some TCP fields share a byte then group them. As usual, your figure can simply show the frame as a long, thin rectangle. To work out sizes, observe that when you click on a protocol block in the
middle panel (the block itself, not the “+” expander) Wireshark will highlight
the corresponding bytes in the packet in the lower panel, and display the
length at the bottom of the window. You may also use the overall packet size
shown in the Length column or Frame detail block. Note that this method will
not tell you sub-byte positions. [5 points]: Hand in your
drawing of a TCP segment. Step 4: TCP Connection Setup/TeardownThree-Way HandshakeTo see the “three way handshake” in action, look for a TCP segment with the SYN flag on, most likely at the beginning of your trace, and the packets that follow it. The SYN flag is noted in the Info column. You can also search for packets with the SYN flag on using the filter expression “tcp.flags.syn==1”. A “SYN packet” is the start of the three-way handshake. In this case it will be sent from your computer to the remote server. The remote server should reply with a TCP segment with the SYN and ACK flags set, or a “SYN ACK packet”. On receiving this segment, your computer will ACK it, consider the connection set up, and begin sending data, which in this case will be the HTTP request. Your exchange should follow this pattern, though it is possible that it differs slightly if a packet was lost and must be retransmitted. [10 points] : Draw a time sequence
diagram of the three-way handshake in your trace, up to and including the first
data packet (the HTTP GET request) sent by your computer when the connection is
established Put your computer on the left side and the remote server on the
right side. As usual, time runs down the page, and lines across the page indicate
segments. The result will be similar to diagrams such as Fig. 6-37. Include the following features on your diagram: Š The Sequence and ACK number, if present, on each segment. The ACK number is only carried if the segment has the ACK flag set. Š
The time in
milliseconds, starting at zero, each segment was sent or received at your
computer. Š
The
round-trip time to the server estimated as the difference between the SYN and
SYN-ACK segments. Connection OptionsAs well as setting up a connection, the TCP SYN packets negotiate parameters between the two ends using Options. Each end describes its capabilities, if any, to the other end by including the appropriate Options on its SYN. Often both ends must support the behavior for it to be used during data transfer. Answer the following question: [5 points]: What TCP Options are carried on the SYN
packets for your trace? Common Options include Maximum Segment Size (MSS) to tell the other side the largest segment that can be received, and Timestamps to include information on segments for estimating the round trip time. There are also Options such as NOP (No-operation) and End of Option list that serve to format the Options but do not advertise capabilities. You do not need to include these formatting options in your answer above. Options can also be carried on regular segments after the connection is set up when they play a role in data transfer. This depends on the Option. For example: the MSS option is not carried on each packet because it does not convey new information; timestamps may be included on each packet to keep a fresh estimate of the RTT; and options such as SACK (Selective Acknowledgments) are used only when data is received out of order. For fun, look at the options on data packets in your trace. FIN/RST TeardownFinally, the TCP connection is taken down after the download is complete. This is typically done with FIN (Finalize) segments. Each side sends a FIN to the other and acknowledges the FIN they receive; it is similar to the three-way handshake. Alternatively, the connection may be torn down abruptly when one end sends a RST (Reset). This packet does not need to be acknowledged by the other side. [10 points]: Draw a picture of the teardown in your trace, starting from
when the first FIN or RST is issued until the connection is complete. As
before, show the sequence and ACK numbers on each segment. If you have FINs
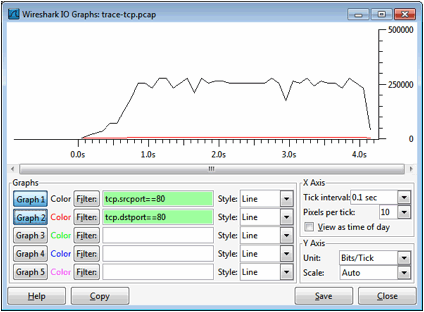
then use the time difference to estimate the round-trip time.Hand in your drawings and the answers to the above questions. Step 5: TCP Data TransferThe middle portion of the TCP connection is the data transfer, or download, in our trace. This is the main event. To get an overall sense of it, we will first look at the download rate over time. Under the Statistics menu select an “IO Graph”. By default, this graph shows the rate of packets over time. Tweak it to show the download rate with the changes given below. You might be tempted to use the “TCP Stream Graph” tools under the Statistics menu instead. However, these tools are not useful for our case because they assume the trace is taken near the computer sending the data; our trace is taken near the computer receiving the data. Š On the x-axis, adjust the tick interval and pixels per tick. The tick interval should be small enough to see into the behavior over the trace, and not so small that there is no averaging. 0.1 seconds is a good choice for a several second trace. The pixels per tick can be adjusted to make the graph wider or narrower to fill the window. Š On the y-axis, change the unit to be Bits/Tick. The default is Packet/Tick. By changing it, we can easily work out the bits/sec throughput by taking the y-axis value and scaling as appropriate, e.g., 10X for ticks of 0.1 seconds. Š Add a filter expression to see only the download packets. So far we are looking at all of the packets. Assuming the download is from the usual web server port of 80, you can filter for it with a filter of “tcp.srcport==80”. Don’t forget to press Enter, and you may need to click the “Graph” button to cause it to redisplay. Š To see the corresponding graph for the upload traffic, enter a second filter in the next box. Again assuming the usual web server port, the filter is “tcp.dstport==80”. After you press Enter and click the Graph button, you should have two lines on the graph. Our graph for this procedure is shown in the figure below. From it we can see the sample download rate quickly increase from zero to a steady rate, with a bit of an exponential curve. This is slow-start. The download rate when the connection is running is approximately 2.5 Mbps. You can check your rate estimate with the information from wget/curl. The upload rate is a steady, small trickle of ACK traffic. Our download also proceeds fairly steadily until it is done. This is the ideal, but many downloads may display more variable behavior if, for example, the available bandwidth varies due to competing downloads, the download rate is set by the server rather than the network, or enough packets are lost to disrupt the transfer. You can click on the graph to be taken to the nearest point in the trace if there is a feature you would like to investigate.
Figure 5: TCP download rate over time via an IO graph Answer the following questions to show your understanding of the data
transfer: [5 points]: What is the rough data rate in the download
direction in packets/second and bits/second once the TCP connection is running
well? [5 points]: What percentage of this download rate is
content? Show your calculation. To find out, look at a typical download
packet; there should be many similar, large download packets. You can see how
long it is, and how many bytes of TCP payload it contains. [5 points]: What is the rough data rate in the upload
direction in packets/second and bits/second due to the ACK packets? Inspect the packets in the download in the middle of your trace for these
features: Š You should see a pattern of TCP segments received carrying data and ACKs sent back to the server. Typically there will be one ACK every couple of packets. These ACKs are called Delayed ACKs. By delaying for a short while, the number of ACKs is halved. Š Since this is a download, the sequence number of received segments will increase; the ACK number of subsequently transmitted segments will increase correspondingly. Š Since this is a download, the sequence number of transmitted segments will not increase (after the initial get). Thus the ACK number on received segments will not increase either. Š Each segment carries Window information to tell the other end how much space remains in the buffer. The Window must be greater than zero, or the connection will be stalled by flow control. Answer the following
question: [5 points]: If the most recently received TCP segment
from the server has a sequence number of X, then what ACK number does the next
transmitted TCP segment carry? As well as regular TCP segments carrying data, you may see a variety of other situations. You can sort the trace on the Info column and browse the packets of type “[TCP xxx ...”. Depending on the download, you may see duplicate acks, out of order data, retransmissions, zero windows, window updates, and more. These segments are not generally distinguished by flags in the TCP header, like SYN or FIN segments. Instead, they are names for situations that may occur and be handled during transport. [END] |