Lecture 25 - Web Security
What Security?
until now, we have assumed:
- valid user input
- non-malicious users
- nothing will ever go wrong
this is unrealistic!

The real world
in order to write secure code, we must assume:
- invalid input
- evil users
- incompetent users
- everything that can go wrong, will go wrong
- There are hordes of people out to get you
the security mindset: assume nothing; trust no one
Attackers' goals
- Read private data (user names, passwords, credit card numbers, grades, prices)
- Change data (change a student's grades, prices of products, passwords)
- Spoofing (pretending to be someone they are not)
- Damage or shut down the site, so that it cannot be successfully used by others
- Harm the reputation or credibility of the organization running the site
- Harass users of your site
- Spread viruses and other malware
Some kinds of attacks
- Denial of Service (DoS): Making a server unavailable by bombarding it with requests.
- Social Engineering: Tricking a user into willingly compromising the security of a site (e.g. phishing)
- Privilege Escalation: Causing code to run as a "privileged" context (e.g. "root").
- Information Leakage: Allowing an attacker to look at data, files, etc. that he/she should not be allowed to see.
- Man-in-the-Middle: Placing a malicious machine in the network and using it to intercept traffic.
- Session Hijacking: Stealing another user's session cookie to masquerade as that user
- Cross-Site Scripting (XSS) or HTML Injection: Inserting malicious HTML or JavaScript content into a web page.
- SQL Injection: Inserting malicious SQL query code to reveal or modify sensitive data
SQL Injection
Demo
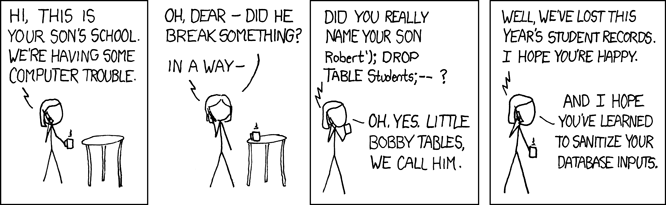
Securing against SQL injection
Escape the string before you include it in your query
quote returns a SQL-escaped and quoted version of a string
$username = $db->quote($_POST["username"]);
$password = $db->quote($_POST["password"]);
$query = "SELECT name, ssn, dob FROM users
WHERE username = $username AND password = $password";
You can also use prepare and execute to protect against SQL injection
HTML Injection
Demo
Learn more from a cross scripting game: https://xss-game.appspot.com/
Securing against HTML Injection
Instead of setting innerHtml, set textContent
mydiv.textContent = "This wont show as html";
<strong>This wont show as html</strong>
output
textContent will not let any of the string be interpreted as html.