Key Words: computer security, virus, hacker, spyware, patch, spam filter, Windows Update.
The Internet can be an unpredictable, and sometimes unsafe, place. In the real world, you wouldn't leave your house unlocked, your car door open, or your wallet lying around. The same holds true with the Internet, and even a brand new computer is not impervious to worms and viruses. This lab will walk you through the basics of setting up your computer and safeguarding it against some of the uncertainties of the Internet. While it will not make you an instant computer security expert, it will give you a few tools that will help you protect yourself and your computer from some of the things that are out there.
There are three common threats that you may run into while online: viruses, hackers, and spyware. Viruses are malicious programs that can make your computer spam other computers, delete all of your files, or even give someone else complete control over your computer. Hackers are individuals who, for reasons ranging from boredom to being paid by organized crime, write viruses and steal personal data on the Internet. Spyware is like a virus, but instead of deleting or modifying files, may report your personal information (things like your credit card number and your Social Security Number) to other people so that they may steal your identity. This lab will give you the tools to help prevent these three things from happening to you while you are online.
Note that all of the software used in this lab is either free from the provider or available as part of the UW Internet Connectivity Kit (UWICK) package. This software can be downloaded and used on your home computer or laptop to keep it safe from these threats. We highly recommend that you do so!
Before you start working, open a text editor, such as NotePad2. As you encounter the questions, write down your answers in the text file. When you're done, you'll upload the file to the CollectIt drop box.
Good password security is the first line of defense against any sort of threat on the Internet. A bad password will make even the best security system worthless, so it is important to follow a few basics about good password creation:
Many people have a "system" for creating secure passwords. One way to ake a good password is to start with some phrase that is easy for you to remember, but difficult for others to guess.For example, if you like the song "Stairway to Heaven" by Led Zeppelin, you could take the first letters from each word in the line "And she's buying a stairway to heaven" as the basis for your password, which would create a password of 'asbasth'. From here, you could mix some upper-case letters in with your password to make it 'aSbAsTh'. To make it a little more complex, you could then replace some of the letters with numbers and special characters that look like the letters they replace, making it '@SbA5Th'. Now, since it's only 7 characters long, we can lengthen it a little by adding an exclamation point, so that it is '@SbA5Th!'.
There are also services online that will help you choose a good password. You may have seen these when setting up an e-mail account. Open your browser and visit Microsoft's Password Checker. Try out a few passwords and see how secure Microsoft thinks they are. Try one of your usual passwords (this webpage does not store your password, but it's good to be thinking about this). Try the method above with a favorite song. Think of a few words in the lyrics of the song and take the letters of each of those words to create a password out of. Then, do some of the above steps to strengthen the password.
Q1. Try this for your favorite song. Think of a few words in the lyrics of the song and take the letters of each of those words to create a password out of. Then, do some of the above steps to strengthen the password. Write down the password you came up with and an explanation of how you created it.
You can also find many programs or online services that generate secure passwords for you. An example would be at this page, a secure password generator with options to add punction, caps, or numerals to our password of specified length. However, we should be wary when using these services as they might be unknowingly storing our generated password to use for malicious purposes. Even though we may have created a secure password, we must always be aware that our password could have been potentially compromised. Thus, it is also good practice to regularly change your password, perhaps once every few months.
Here we will discuss three common e-mail concerns: viruses, "phishing" attacks, and junk mail.
Much of the time, viruses can spread through emails that look like they come from trusted sources. The email may contain enticing messages to download its attachments or click on a link, which eventually ends up infecting your system with a virus. Other times hoaxes can be sent out through trustworthy-looking emails that try and get information about you such as your credit card number. This process of obtaining your information through deception is called "phishing". Spotting these emails is very hard for software to do, and so it's up to you and your skepticism to figure out the good from the bad. Generally, the things to look for in an email message are the same things you should look for when looking at web sites. Here are a few of the ways that you can figure out whether an email is legitimate:
One final thing to remember is to NEVER OPEN EMAIL ATTACHMENTS from people that you do not know. And even if you know the person, it is a good idea to scan the email attachment with an up-to-date virus scanner just to make sure, since a lot of viruses can disguise themselves as being from someone you know.
Q2. Now it's time to put what you just learned into practice. Here and here are two email messages. Using what you just learned, decide which one is real and which one is fake. Write down your answer, and the reasons why you chose it.
Junk e-mail or "spam" is a problem that affects anyone who uses e-mail. It's also a problem that is unlikely to go away soon. Since e-mail is essentially free to use, it's profitable to send e-mail advertisements even if only a few people respond.
There are multiple ways of handling junk e-mail. Many e-mail clients have built in spam filtering. If you use your UW mail, you can turn on the university's server-side spam filter.
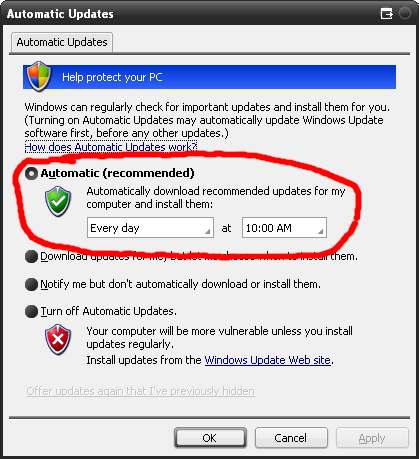
An additional way to protect your computer is to install patches for your operating system. A lot of times, there are flaws that are found in the code of operating systems like Windows or Mac OS, and so it is important to stay up-to-date on all of the latest patches so that your computer is protected against these flaws. Let's practice updating Windows now (though more than likely the lab machines do not need updating at the moment
In order to keep your computer up to date automatically, you can also enable automatic updates with Windows Update.

Q3. When was the last time the machine was updated?
Q4. Does this machine have the GDI+ Detection Tool installed?
McAfee VirusScan is the virus protection software used at the University. You can acquire it for $1 at the University Bookstore or download it as part of UWICK.
Anti-virus software performs two primary functions:
Every week new viruses, worms, and other nasty software appear on the Internet. Because of this, simply installing anti-virus software is not enough. You need to update your VirusScan definitions - the files that tell anti-virus software how to detect a specific virus - daily or weekly. McAfee VirusScan definitions can be updated automatically or manually. We will show you how to do both because sometimes a nasty virus spreads so fast that you should not wait for the auto-update feature to update your definitions.
To manually update your virus definitions in McAfee VirusScan:

Before you update, answer the following question:
Q5. What was the last time that this computer had its virus definitions updated?

To verify your Windows McAfee VirusScan software is automatically being updated with the latest virus definitions, or to enable automatic updates to your anti-virus software:
Spyware is a common problem for Windows computers. Similar to a virus, spyware is software that has been installed onto your system without your knowledge. Unlike a virus, spyware is less overtly destructive and is therefore it is much less obvious when you are infected by spyware. In truth, many problems that Windows users have with their programs and computers may be traced back to spyware. This software often uses up system resources such as memory and processor time and can corrupt files. While some antivirus software now has the ability to look for and remove spyware, the best spyware detectors and removers are not the best antivirus programs. Therefore, we will focus on scanning and removing spyware with specialized antispyware tools.
For this part of the lab we will use Windows Defender, a (currently) free spyware scanner from Microsoft. You can also download Defender to use at home from the link below.
Note that the the installer page for Defender requires you to install a browser plugin in order to validate your copy of Windows. This is more complicated in Firefox and Mozilla than for Internet Explorer. We recommend that you use IE to download Defender in this section.


Question |
Possible Points |
|---|---|
| Q1. Password made up of first letter of each word in favorite song. | 3 |
| Q2. Decide which one is real and which one is fake. Write down your answer, and the reasons why you chose it. | 3 |
Q3. When was the last time the machine was updated? |
3 |
| Q4. Does this machine have the GDI+ Detection Tool installed? [No, Don't know. Not sure.] | 3 |
| Q5. What was the last time that this computer had its virus definitions updated? | 3 |
| Q6. How is spyware different from viruses? | 5 |
When you've finished the exercise, copy your answer file to a lab14 directory in your fit100 directory on dante.
To submit, upload it to the Catalyst Collect-It Turn-in Area on the Course Calendar and select this lab number.